Which of the Following Best Describes Public Key Encryption
Which of the following best describes a feature of symmetric encryption. Asymmetric key encryption uses both a private and public key to encrypt and decrypt messages.
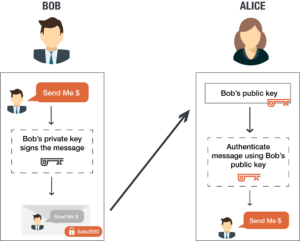
Public And Private Encryption Keys Preveil
Which of the following activities poses the greatest personal cybersecurity risk.

. Public key encryption or public key cryptography is a method of encrypting data with two different keys and making one of the keys the public key available for anyone to use. Which of the following best describes an asymmetric key encryption strategy. The process of changing the ciphertext to the plaintext that process is known as decryption.
B 10 Digital certificates are used to. The two types of PKC algorithms are RSA which is an. A Shared key cryptography.
You work for a company that is implementing symmetric cryptography to process payment applications such as card transactions where personally identifiable PII needs to be protected to prevent identity theft or fraudulent. Asymmetric key encryption uses both a private and public key to encrypt and decrypt messages. A digital signature is A.
A unique identification of a sender C. A message sender uses a recipients public key to encrypt a message. A Encryption completely protects your data.
D Withdrawing money from a bank account using an. Asymmetric key encryption uses two private keys to encrypt and decrypt messages. Public key encryption is an encryption method which relies on separate keys for encrypting and decrypting information.
The Correct Answer is- A. Which of the following best describes the Public Key Cryptography Standards. C Reserving a hotel room by e-mailing a credit card number to a hotel.
Symmetric cryptography is also known as __________. An authentication of an electronic record by tying it uniquely to a key only a sender knows D. A Making a purchase at an online store that uses public key encryption to transmit credit card information.
E none of the above Answer. Public key encryption makes use of certain types of problems which are easier for humans to solve than. B Encryption assists in an overall security program.
Asymmetric key encryption uses three separate keys for both encryption and decryption. Asymmetric key encryption uses a single key for both encryption and decryption. The other key is known as the private key.
Which of the following best describe the difference between public key cryptography and public key infrastructure. Only one person can encrypt with the public key and anyone can decrypt with the private key 8. Public Key Encryption.
9 The following statement best describes encryption on the internet. A collection of varying technologies and policies for the creation and use of digital certificates. Public key encryption is an encryption method which relies on separate keys for encrypting and decrypting information.
Data encrypted with the public key can only be decrypted with the private key and data encrypted with the private key can only be decrypted with the public key. Public key encryption is a highly secure encryption scheme that in which a single shared key is used by both the sender and receiver of the message. Public key cryptography PKC is an encryption technique that uses a paired public and private key or asymmetric key algorithm for secure data communication.
1 answer below. Uses only one key to encrypt and decrypt data. B Public key cryptography.
Public key cryptography is the use of an asymmetric algorithm while public key infrastructure is the use of a symmetric algorithm. Practice exam questions 6 7. A de facto standard that defines a framework for authentication services by a directory.
Asymmetric is a form of Cryptosystem in which encryption and decryption are performed using different keys-Public key known to everyone and Private key Secret key. Asymmetric key encryption uses a single key for both. A bit string giving identity of a correspondent B.
A Public Key database ensures 3rd party accountability of security. D Encryption only works for email. Choose the answer that is NOT a feature of Public Key Cryptography.
This is known as Public Key Encryption. To decrypt the senders message only the recipients private key may be used. Asymmetric key encryption uses two private keys to encrypt and decrypt messages.
C Encryption only works on an intranet. An encrypted signature of a sender 9.

Public And Private Encryption Keys Preveil

Public Key Cryptography Explained Sectigo Official

Solved 7 Which Of The Following Is True About Public Key Chegg Com
No comments for "Which of the Following Best Describes Public Key Encryption"
Post a Comment